Approaches to Message Authentication
Going by their acronyms SPF DKIM and DMARC the three are difficult to. It gives a clean approach to writing APIs.

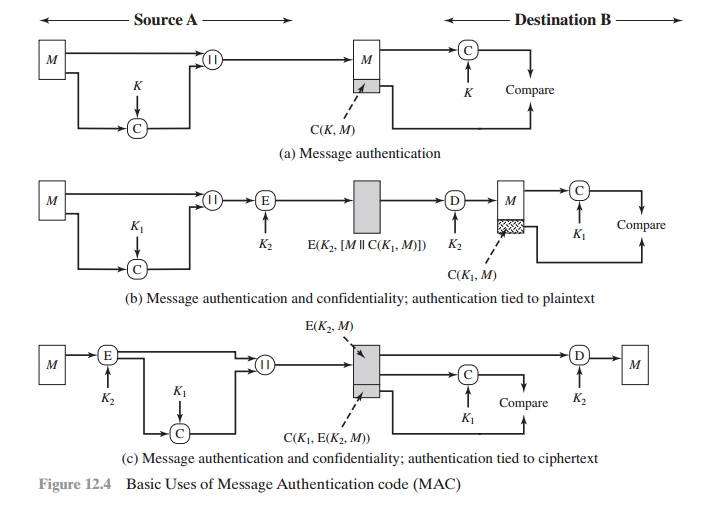
Public Key Cryptography And Message Authentication Ppt Download
However most authentication information is transmitted in the message header so it isnt visible.
. When using redirects with MSAL it is mandatory to handle redirects with either the MsalRedirectComponent or handleRedirectObservableWhile we recommend MsalRedirectComponent as the best approach both approaches are detailed below. The hash code is again sent back to AS. The Galois Message Authentication Code GMAC is the GCM standalone authentication scheme.
Number The amount of time it took to receive a response in the authentication event in seconds. To acomplish the authentication you can basically use different approaches. All are welcome all can succeed - each in their own way.
Private information diffusion that will pose a paramount security concern. With the auth_request directive line 7 we can for example have authentication handled by an external authentication server such as OAuth 20 token introspection. The ClientAuthenticationException is raised and it has a message attribute that describes why authentication failed.
The variety of applications results in a large amount of users. For some end-users even setting up a mobile phone to receive a one-time password via text message can be an. A second approach is to modify the Cray file system as described below in order to prevent Slurm-specific files needing to be re-resolved over.
From O365 import Account credentials client_id client_secret account Account. With HMAC you can achieve authentication and verify that data is correct and authentic with shared secrets as opposed to approaches that use signatures and asymmetric cryptography. Again its about the evolution of security.
Follow the links above to learn more about the specifics of each of these authentication approaches. However there are some cases where you might. Requiring secure MFA sign-on.
The amount of time for the completion of the authentication event in seconds. Username and password before sending. The advantage of multi-factor authentication is that in most cases its.
In the rest of this article well introduce the commonly used DefaultAzureCredential and related topics. In most scenarios the default context path is all you would want. The preloadjs file is where you will mediate the communication between the main and the renderer processcontextBridgeexposeInMainWorld allows you to define an API in this case called electron that your renderer can invokeThis file has access to both the renderer and main process and can delegate messages from the renderer to the main process.
Two approaches exist to address this issue. User authentication is a significant factor in the IoT environment as it allows the user. The user sends a message to KDC requesting keys so that the user can prove its authenticity and access the services of the Network.
Use multi-factor authentication. Email authentication requires the sending and receiving servers to coordinate and cooperate. Some of the new approaches being tested and used include.
Quick example on sending a message. One is to disable the flushing of caches which can be accomplished by adding LaunchParameterslustre_no_flush to your Slurm configuration file slurmconf. The ticket will be in encrypted form.
Over 20 years of experience in authentication backed by a network that connects the world. Hash-based message authentication code or HMAC is a cryptographic authentication technique that uses a hash function and a secret key. However you can use the simple OSA protocol together with more advanced network security authentication approaches like EAP and PSK authentication.
Token based authentication scheme where anyone in possession of a valid token can gain access to the associated secured resources in this case our API. Multi-factor authentication MFA also known as two-step verification requires people to use a code or authentication app on their phone to sign into Microsoft 365 and is a critical first step to protecting your business data. 2 step authentication with user consent.
In this example we instead add the logic for validating API keys to the toplevel API gateway configuration file in the form of the following location block called _validate_apikey. Our employees come with different backgrounds and experiences resulting in many different approaches that are part of our success. The PBA prevents anything being read from the hard disk such as the operating system until the user has confirmed they have the correct.
Pre-boot authentication PBA or power-on authentication POA serves as an extension of the BIOS UEFI or boot firmware and guarantees a secure tamper-proof environment external to the operating system as a trusted authentication layer. Now AS Authentication server in KDC will send the ticket back to the User. The user will decrypt the message and get the hash code.
The AP decrypts the message and compares the result with the original challenge text. 5 Primary Email Authentication Methods. Follows on from Basic Authentication but is more secure as it applies a hash function to any sensitive data eg.
Using redirects in MSAL Angular v2. The computer encrypts the challenge text with its WEP key and transmits the message back to the AP. By default Spring boot has as the context path.
Internet of Things IoT has become one of the most significant technologies in recent years because of possessing the diverse application domains. This means that authentication shouldnt impact the quality of your email content. 2 step authentication with user consent.
From this perspective quantum key distribution QKD approaches offer considerable promise. String The human-readable message associated with the authentication action success or failure. Despite making some progress a trio of email security protocols has seen a rocky road of deployment in the past year.
You cant go wrong. A dedicated handleRedirectObservable component. If you wish to overridechange the context path then you can use one of the following approaches.

Unit 2 Public Key Cryptography And Message Authentication Ppt Download
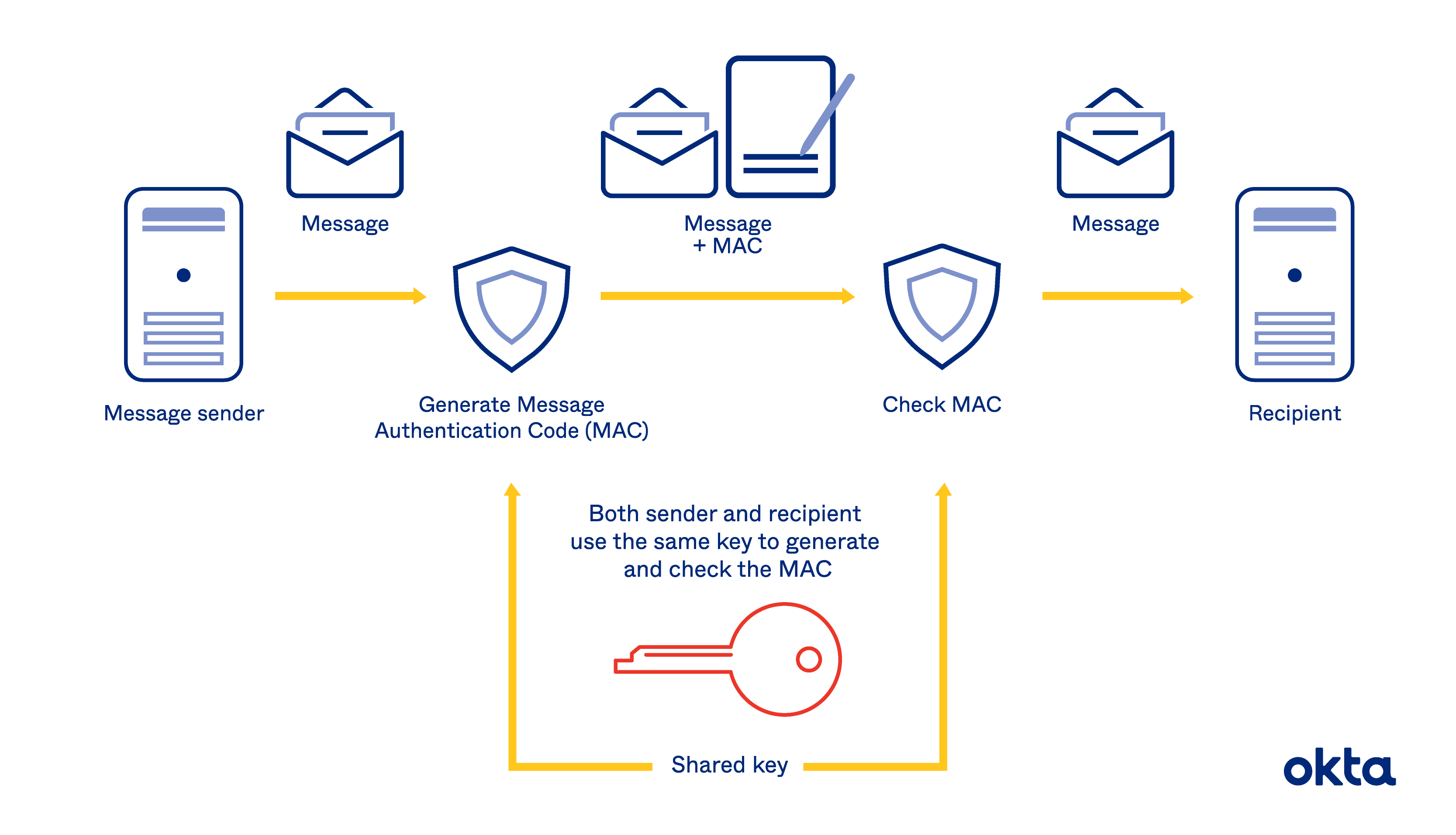
Hmac Hash Based Message Authentication Codes Definition Okta
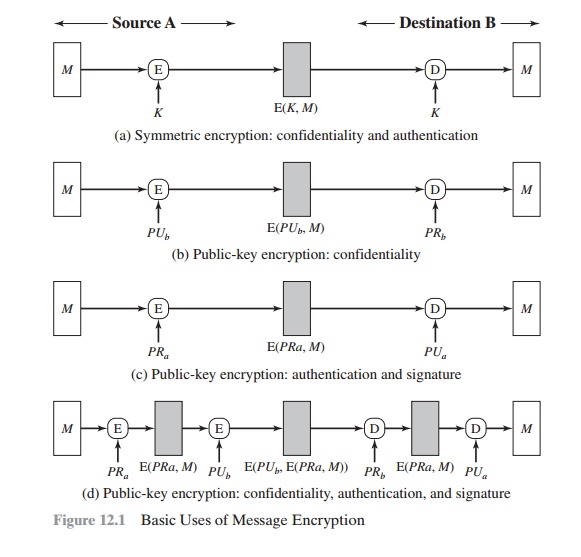
Message Authentication Functions

Message Authentication Functions

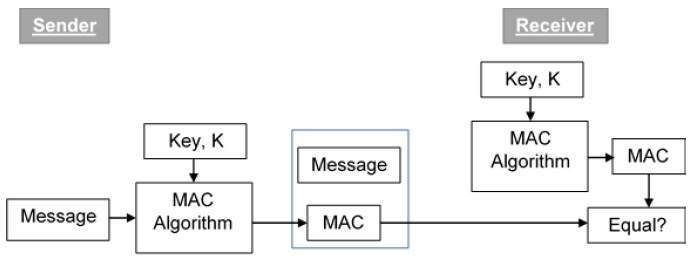
Comments
Post a Comment